This is part 4/4 in our series on one of the most exploited issues in Web3: Offline signatures.
In Part 1 we investigated how attackers abuse these issues with OpenSea, the largest NFT marketplace. In Part 2 we exposed new attack vectors that allow attackers to exploit offline signatures in novel ways, including the stealing of ERC-20 tokens. In Part 3 we shared our suggested solution published as an official Ethereum (EIP) standard draft: EIP-6384.
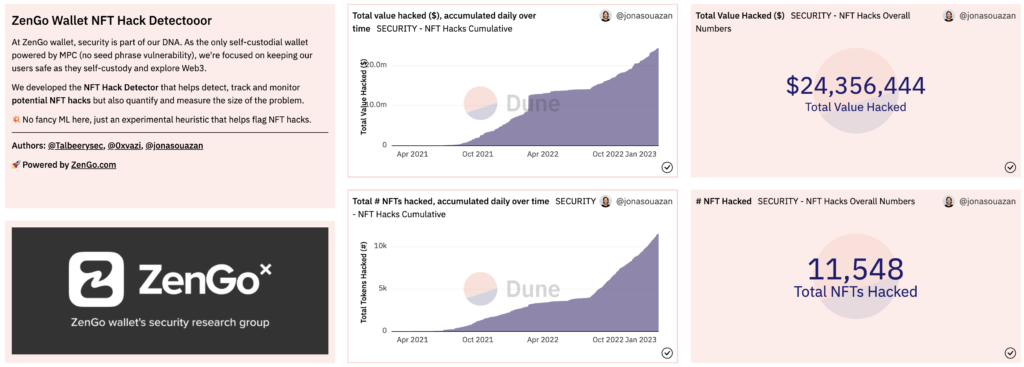
Today, we share the first real-time dashboard to enable the community to monitor the phenomena of NFT hacking via offline signatures on the OpenSea marketplace. Our findings, based on this dashboard and further research, shows that the size of this NFT attack vector is significantly increasing over time, already resulting in $25 million worth of NFTs stolen.
 Updated as of February 20, 2023; 👆 on image for link
Updated as of February 20, 2023; 👆 on image for link
Using these findings, we were able to alert in advance on the attackers’ account that stole millions of USD worth of NFTs from an industry-leading NFT pioneer.
Our most alarming finding: This trend is not subsiding, but growing and its modus operandi has recently transformed from “spear phishing” to “industrialized dragnet phishing” which affects many victims. Even more alarming, some portions of this industrialized dragnet phishing campaign seems to be closely tied to known North Korean cyber attack groups.
How users are getting scammed with Offline signatures: A short summary
The core problem with offline signature hacks is the indecipherable message displayed to users. This message is not human-readable and phishing sites trick users to sign harmful messages, e.g. sell their precious NFTs for a zero price in OpenSea, or allow hackers access to their funds on Uniswap.
The video below, taken by Zengo wallet’s research team of a live phishing site, shows what such an attack looks like from the victim’s point-of-view.
https://youtu.be/cwBn_EB4PXs
Offline Signature Phishing Attack: Victim’s point of view
As shown above, the suggested message to be signed is hardly comprehensible for normal users and certainly does not hint that the victims are going to sell their NFTs for virtually nothing.
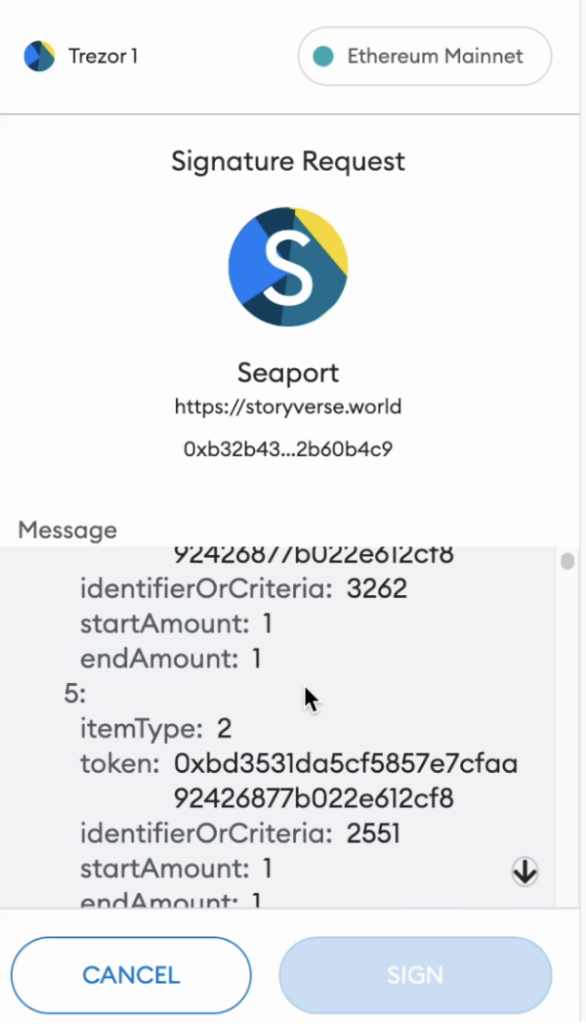
It is important to note, that since offline signed messages are not immediately and directly executed by a smart contract, the standard technique of transaction simulation that solves similar problems for on-chain transactions is not applicable for this case.
For additional background and details, please see Part 1 and Part 2.
Zengo’s OpenSea hack monitoring dashboard: Research methodology
The idea behind our detection rule is very simple: If a valuable NFT was traded through OpenSea for a very low amount compared to its estimated value, then it’s highly likely to be a scam.
To implement this query, we turned to Dune Analytics. Dune Analytics provides a powerful query engine as well as useful abstractions to allow data scientists to write powerful queries on the blockchain data.
As some Dune community members had already created a table to monitor all OpenSea marketplace trades, all we had to do was to express our abstract detection rule idea in a SQL query on this table.
In order to measure how far an NFT was traded from its estimated floor price, we created a metric called the floor ratio, where we divided the actual trade price by our estimated floor price of the collection. (The floor price is the lowest-priced NFT within an NFT project).
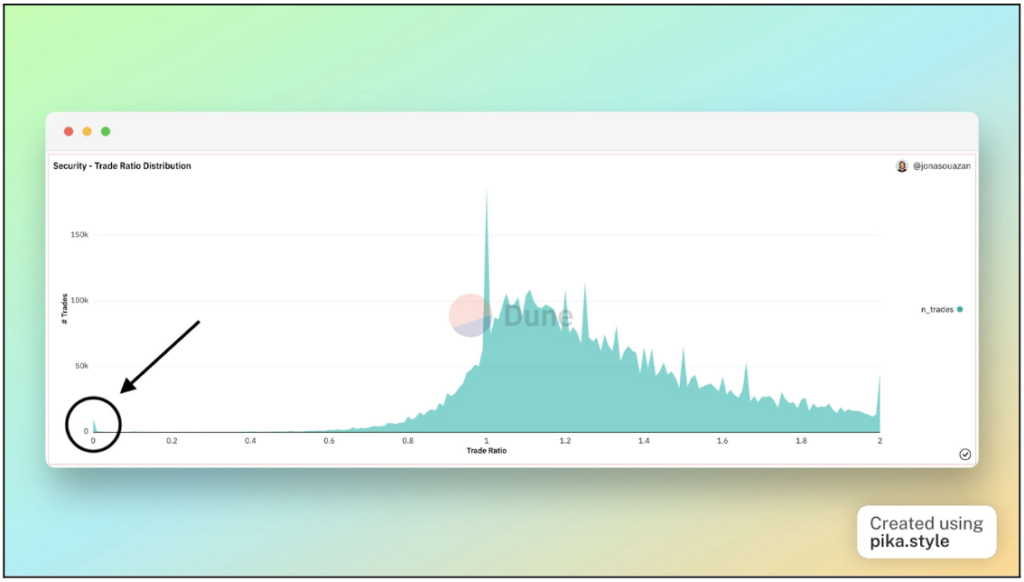
We have refined our detection logic with some additional rules to remove some “noise” from our dataset, such as cases that can be attributed to benign human errors, low value NFT collections that manipulated their floor price, and more. For a detailed report on our research methodology please see here.
One of the ways we validated our results against false positives was by manually checking each of our 25 top attacking addresses against the OpenSea website. When an address is suspended from OpenSea the following message is shown:
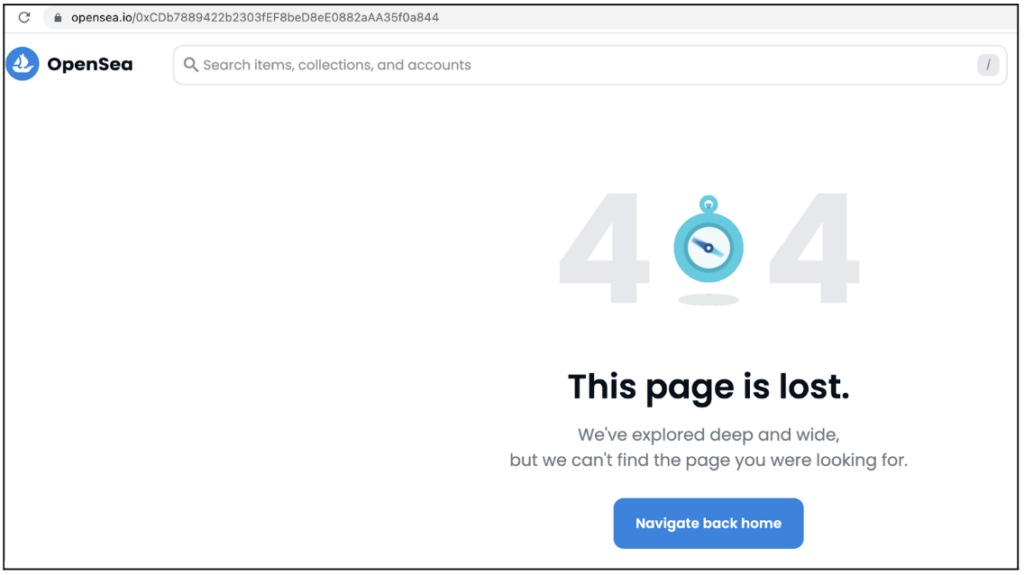 A suspended address page in OpenSea
A suspended address page in OpenSea
At the time of writing, 19 out of 25 addresses (76%) were indeed suspended on OpenSea’s website.
The data was also reviewed for known “flagship” cases of the phenomena such as the February incident, the recent Kevin Rose hack and others.
As we were very conservative in our estimations (e.g. taking into account only high priced NFTs, using floor price as an estimation for NFT value, preferring to be over-restrictive than over-permissive when including a transaction in our dataset), we believe that our estimation of NFT theft can be taken as a lower bound for the true volume of this phenomena.
Zengo’s OpenSea hacks monitoring dashboard: Key Findings
Our dashboard, the Zengo Wallet NFT Hack Detectooor, constantly monitors such attacks as they happen on-chain and display the aggregated amounts.

Zengo’s dashboard (Feb 20th 2023): >$23M lost, >10K top collections’ NFTs stolen
By viewing this dashboard we can quickly arrive at the following conclusions:
- It’s not negligible: Since 2021, more than $23M worth of NFTs have been stolen in such hacks, stealing more than 10,000 of leading NFT collections items.
- It’s growing: Since August 2022 we’ve seen a serious uptick in this abusive activity (we would dive into its reasons below)
The dashboard contains many other searchable and sortable charts. Including:
- An online updating table of each such individual hack with many details with relevant links to Etherscan
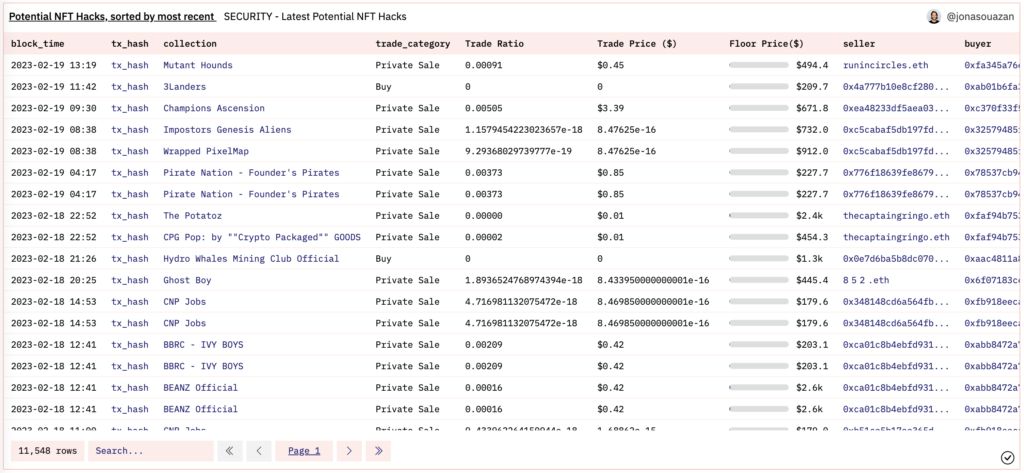
Zengo’s dashboard (Feb 20th 2023): Latest potential hacks chart
- Top attackers, victims, and hacked NFT collections
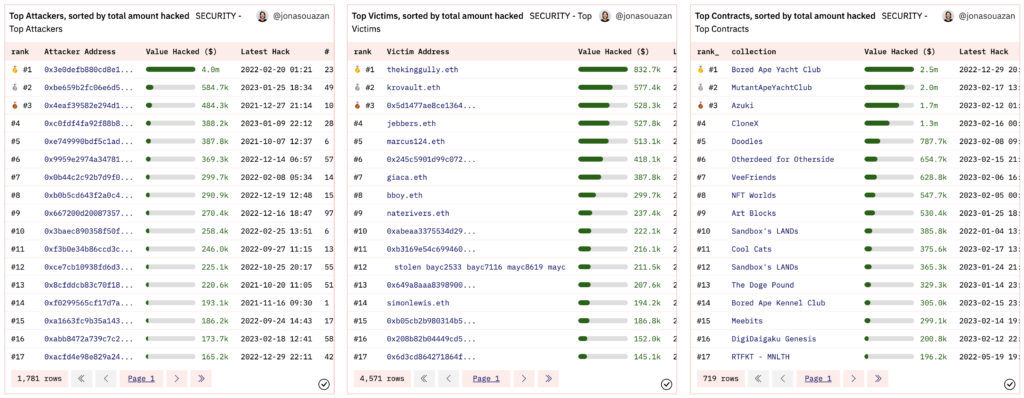
Zengo’s dashboard (Feb 20th 2023): Top attackers, victims and hacked NFT collections
We believe this data, conveniently made available as a public dashboard with multiple charts and graphs, can serve as a highly valuable resource for other security researchers, NFT communities (that can filter the data to include only their NFT collections) and wallet users.
How Zengo uses the dashboard results for advanced alerts
Some contents of this dashboard may be used for threat intelligence. That’s exactly what we did when reporting some of our findings to Etherscan on January 17th, 2023, including address 0x80a48d75Daf26f835d4E0EbBF595a7D7dDeE6E80
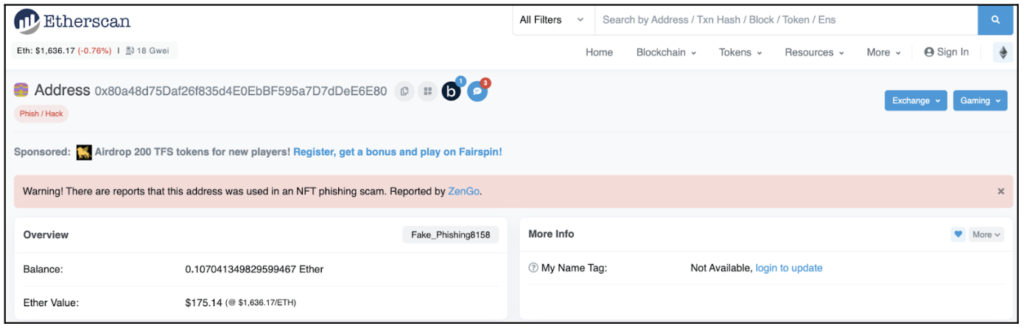
0x80a48d75Daf26f835d4E0EbBF595a7D7dDeE6E80 Reported by Zengo https://etherscan.io/address/0x80a48d75Daf26f835d4E0EbBF595a7D7dDeE6E80
A week later, this very same address had abused Kevin Rose’s phished offline signature to steal 40 of his precious NFTs.
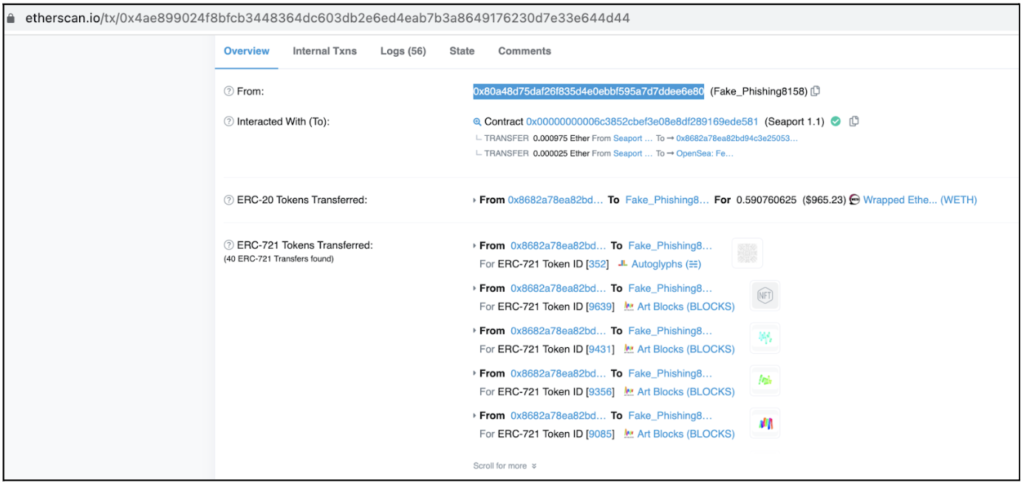
0x80a48d75Daf26f835d4E0EbBF595a7D7dDeE6E80 is Kevin Rose’s NFTs attacker (https://etherscan.io/tx/0x4ae899024f8bfcb3448364dc603db2e6ed4eab7b3a8649176230d7e33e644d44)
Sadly, this threat intelligence was not embedded in any of the relevant systems (i.e. OpenSea contracts) and therefore Kevin’s NFTs were not saved.
Industrialized dragnet phishing: The North Korean connection
The dashboard’s data visualization allowed us to identify a massive uptick in stolen NFTs starting around August 2022.
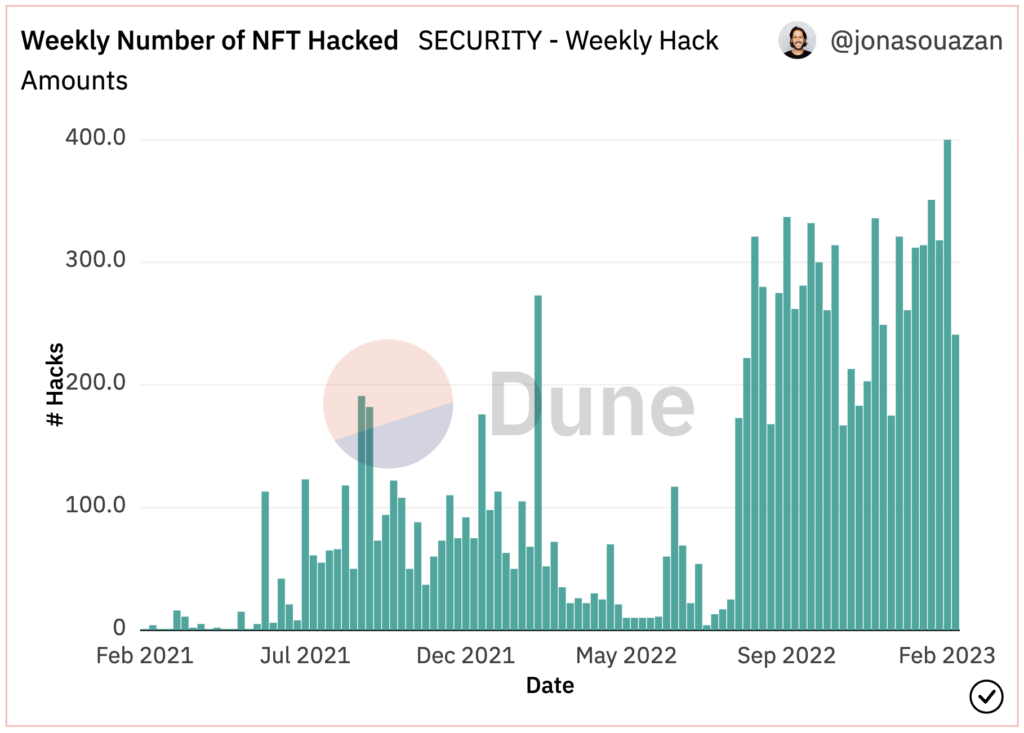
A massive uptick in NFT theft cases, starting on August 2022
Looking deeper into the statistical features of this attack campaign, depicted in the graph below, it is clear this campaign represents a different attack methodology.
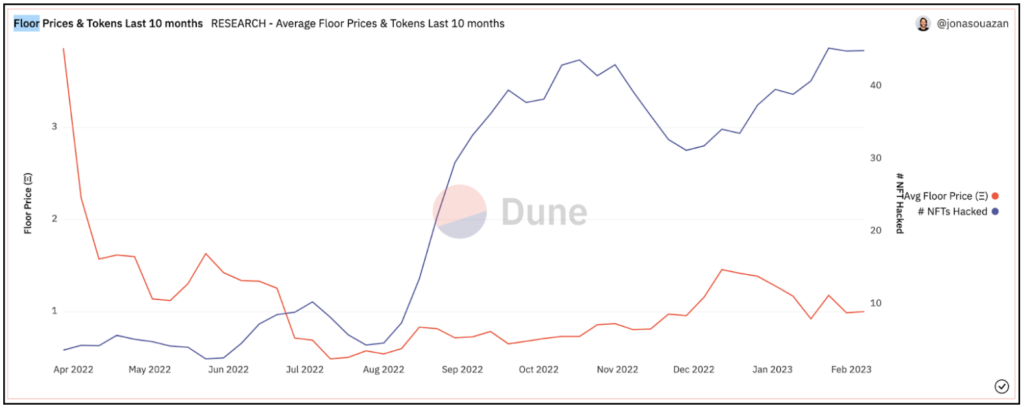
The attack starting on August 22, 2022: Targeting more NFTs even with lower values
Compared to the preceding period, this attack shows much higher volume of NFTs stolen although the average value of each NFT has significantly declined.
To use the very appropriate “fishing” methodology: While previous attackers were spear-phishing by selectively targeting a few high net worth victims and attacking them, this new campaign appears as industrialized mass dragnet phishing: Targeting a much wider audience of victims and non-selectively catching small and big fish.
Such an ongoing industrialized campaign also requires some serious infrastructure to maintain and replace phishing sites as they are constantly getting blocked and deal with the money laundering of the received profit.
Unlike the spike in stolen value in February 2022, fully explained by a single attack operation and properly documented in press publications, this ongoing industrial campaign was not easily mapped to an already known and reported hack.
The breakthrough came when we were able to correlate one of the leading attackers to another threat intelligence report by SlowMist. Last December, SlowMist released a report claiming North Korea was behind many NFT phishing attacks. They were able to get to such attribution by following the infrastructure of the phishing websites and connecting them to other known North Korean resources.
The leading Ethereum address discussed in the report was 0xC0fdF4fA92f88b82CcBeBFC80fbE4EB7E5a8e0ca.
The same address is also #4, in our “top attackers” list:
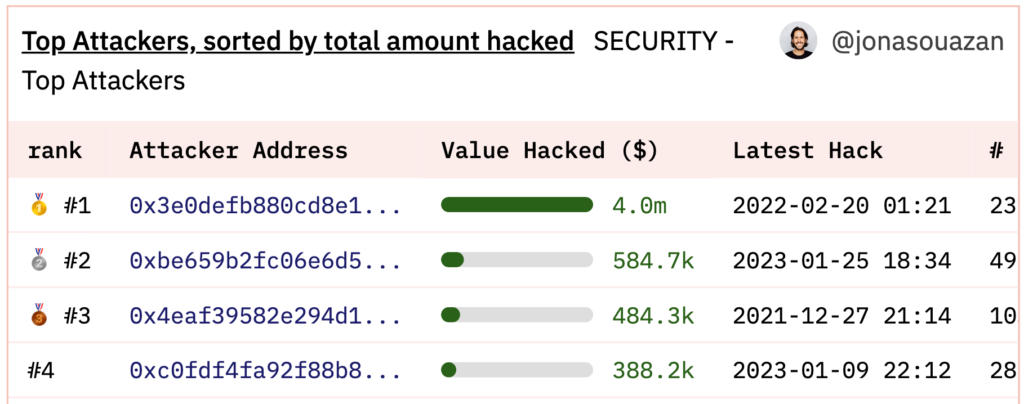 0xC0fdF4fA92f88b82CcBeBFC80fbE4EB7E5a8e0ca is the #4 top attacker
0xC0fdF4fA92f88b82CcBeBFC80fbE4EB7E5a8e0ca is the #4 top attacker
We had shared with SlowMist’s research team several other attacker addresses that have been highly active in the time period since August and they have confirmed their ties to North Korea phishing infrastructure or to other addresses with such ties.
An additional group that is involved in this “dragnet” phishing campaign is the notorious “Monkey drainer” group which, according to SlowMist, started its operation in August too.
Next steps: It’s time for our industry to act!
By quantifying NFT thefts via OpenSea’s smart contract and tracking offline signature abuse for the first time, it is clear this problem is important and growing.
As such, it must be solved.
It should be noted this is not a problem in OpenSea only, but for every protocol that uses offline signatures. There are already many of them (e.g. UniSwap) and it is even gaining popularity as offline signatures generally allow for a better user experience.
Therefore, we believe that it’s time to make Web3 a safer place for everyone, and solve this offline signature vulnerability and especially its unreadability for users.
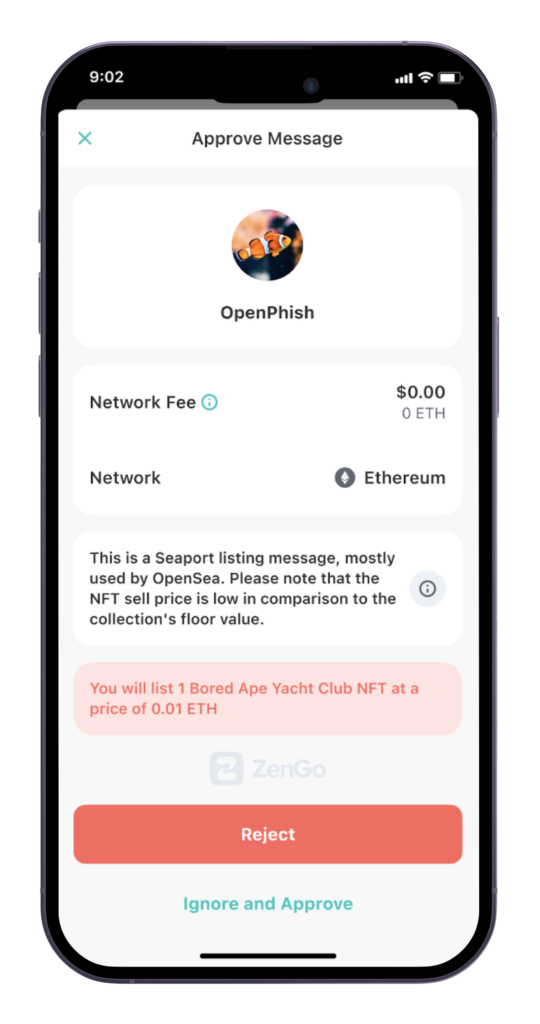 EIP-6384 compliant user experience: The danger is clear!
EIP-6384 compliant user experience: The danger is clear!
One of the most promising directions to achieve this goal is by supporting EIP-6384, as described in Part 3.
Please reach out to us with questions, comments, or partnership ideas: Either publicly via the EIP’s discussion thread on ethereum-magicians 🧙 or privately via [email protected].
Follow Zengo on Twitter for latest updates: @Zengo
Learn more about Zengo X, our open-source MPC library, and github here.
