As part of our ongoing research in the blockchain areas, we set our focus on QR code, as we are adding QR code support for Zengo wallet soon.
As we always do, we explored also the security aspects of this feature and found some reports on QR related scams. We wanted to check how prevalent this phenomenon and to our surprise, we found out that 4 out of the first 5 results presented when querying Google were leading to scammers site.
These sites generate a QR code that encodes an address controlled by the scammers, instead of the one requested by the user, thus directing all payments for this QR code to the scammers.
To protect users, we had shared the technical details of our findings with several threat intelligence providers.
QR codes in crypto
According to cryptocurrencyfacts.com: “A QR code is a simple, fast, and secure way to share an address when transferring cryptocurrency between two devices. This is especially useful in face-to-face point-of-sale transactions because copy and paste isn’t an option and it avoids having to type in very long codes by hand (if you get even one character wrong, it won’t work).
- The recipient needs to display the QR code of the address they want a specific cryptocurrency sent to. This is done with software, either merchant software designed for crypto or a wallet app.
- The sender needs to scan the recipient’s QR code. Specifically, they need to open a wallet app that has a balance of the cryptocurrency being requested, enter the amount they want to send, select the QR option, scan the recipient’s QR code to get their address, verify everything is correct (the amount being sent AND the address), and then confirm the transaction.”
The scam
The scam is dead simple. The scammy QR generator just displays a QR of their address instead of the victims’.
We requested a QR for address 18Vm8AvDr9Bkvij6UfVR7MerCyrz3KS3h4
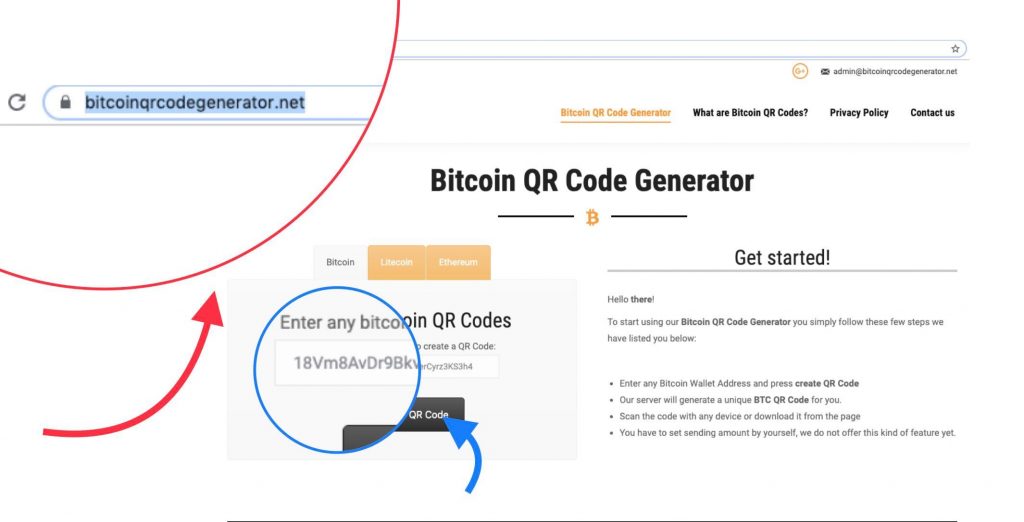
But we got a QR code that matches another address
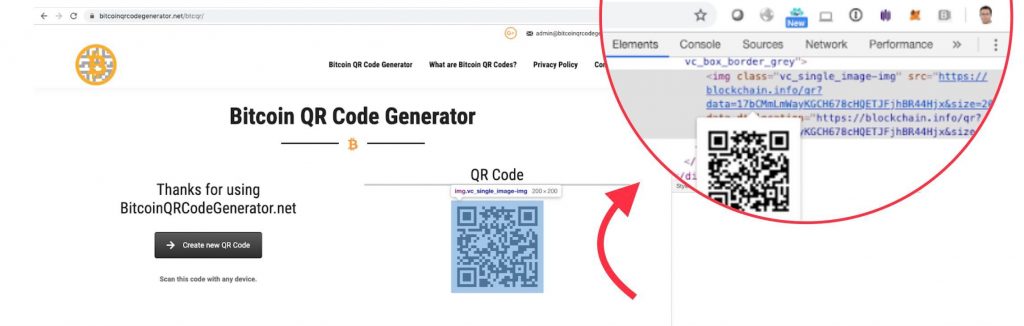
An interesting observation, shown in the picture above, is that the scammers do not even bother with generating their fake QR themselves, instead they shamelessly call a blockchain explorer api (https://blockchain.info/qr?data=17bCMmLmWayKGCH678cHQETJFjhBR44Hjx&size=200) to generate the QR for their address.
Extra tricks that scammers use
Some scammers are not just creating a QR code that leads to their address but also add some extra elements to their scam:
- Customizing the address: Bitcoin supports several addresses formats. Most notably, regular addresses start with ‘1’, pay to script start with ‘3’ and Bech32 addresses start with ‘bc’. Some scamming sites create a QR code in the same format of the requested address, probably to escape detection if the victim lightly verifies the address.
- Changing address on the clipboard: Some scamming sites put their scammy address in the clipboard, so if victims verify the QR code by pasting the value in the clipboard, thinking it’s the address they previously copied to get a QR for, it will match
Are these scams successful? Yes!
Due to the public nature of the Bitcoin blockchain, we were able to gather some statistics on the success of these scams.
Summing up the balances of the scammy addresses we had observed, we found out about scams worth about $20K. We assume they are just the tip of the iceberg, as scammers probably change their addresses to avoid detection and blacklisting.
Recommendations for users:
If you need to export your address as QR:
- Don’t google it! If you need a QR code, use a known site, such as your favorite block explorer.
- Verify: Before sharing the QR, scan it with a wallet app and verify the scanned address is your original address.
- Threat intelligence service: Using a threat intelligence service as a browser addon ( e.g. MetaCert’s Cryptonite) and wallet that alerts on scammy sites and addresses can be useful sometimes, but is not a silver bullet as these services coverage cannot be hermetic.
Technical details for threat intelligence services:
To help services that would like to blacklist such services we are sharing the technical details of this sites and the currently associated addresses.
We have already updated MetaCert’s Cryptonite.
| URL | Crypto addresses |
| hxxps://bitcoinqrcodegenerator.net/ | 17bCMmLmWayKGCH678cHQETJFjhBR44Hjx |
| hxxps://btcfrog.com/ | 14ZGdFRaCN8wkNrHpiYLygipcLoGfvUAtg, 35mJx4EeEY7Lnkxvg1Swn1eSUN1TtQsQ3, bc1qs4hcuqcv4e5lcd43f4jsvyx206nzkh4az05nds |
| hxxps://bitcoin-qr-code.net | 1KrHRyK9TKNU4eR5nhJdTV6rmBpmuU3dGw |
| hxxps://mybitcoinqrcode.com/ | 1Gg9VZe1E4XTLsmrTnB72QrsiHXKbcmBRX |
Parting thoughts
QR code is a very easy way to share data. However, due to the fact that the codes are not humanly readable, it opens an avenue for fraud. Fraud can be on the receiver side when generating as shown here, but also on the sender side if the sender is using a rogue wallet or even a good wallet using a rogue QR implementation.
We believe that we will hear on more QR related fraud in the future and that the cryptocurrency community needs to address these issues and come up with better protections.
