Tl;dr: Recently, PREMINT, an NFT platform used by artists and collectors, was hacked and some of its users lost their NFTs. The total loss is estimated to be in hundreds of thousands of USD. In this blog we briefly describe what happened, highlight some core security issues illuminated by this incident, and, most importantly, show how Zengo’s ClearSign tech protects PREMINT’s users against such attacks.
What happened?
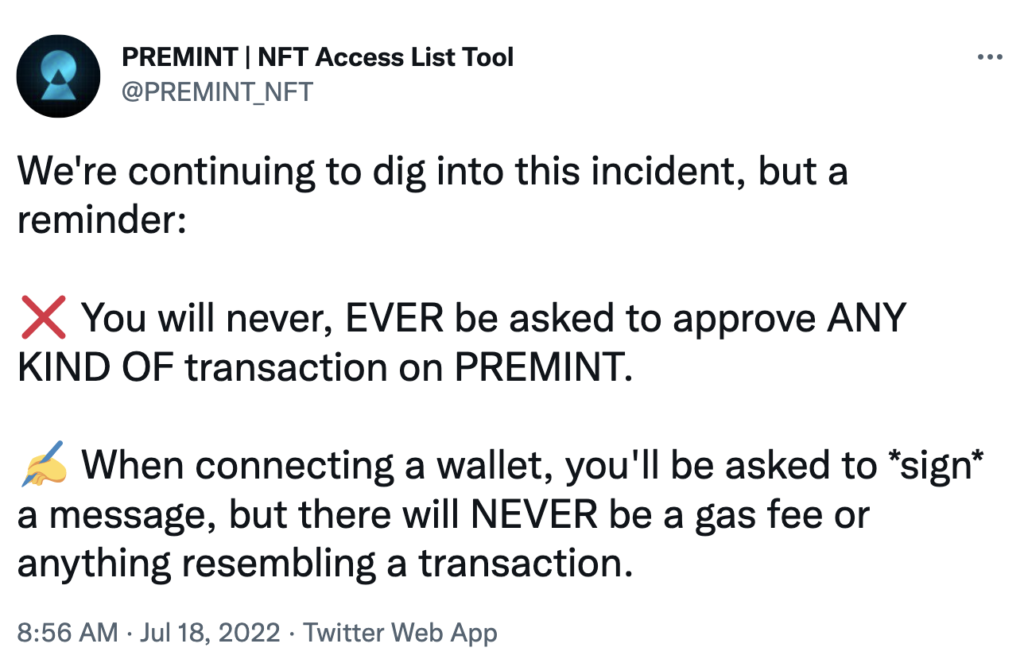
Attackers were able to abuse a vulnerability in PREMINT’s code (allegedly a software supply chain issue, but the exact technical nature of the vulnerability is immaterial) to inject malicious code into PREMINT’s dapp web interface. This malicious code suggested users sign a rogue transaction (“Set Approval For All”). For the users tricked into signing this message, the attackers gained control of all of their NFT assets in a specific NFT collection (e.g. all of their Bored Apes).
The PREMINT website as seen during the attack (source: Twitter.com/kbruh_eth)
Once the attackers gained access to such NFTs, they quickly sold them on NFT marketplaces. The received funds were laundered using mixing services, such as Tornado.cash.
During the attack, the PREMINT team communicated with their users over social media, reminding them that PREMINT will only ask for offline signatures required to verify a user’s identity, but never for an on-chain transaction.
PREMINT’s message to their users (source: https://twitter.com/PREMINT_NFT)
However, this kind of messaging on social media is of course very limited. Not all users will read this message, and also some of them will not get this distinction, or forget about it when actually presented with the rogue transaction.
PREMINT would have probably preferred to prevent such unintended transactions on their website. In security, this sort of procedure is called “hardening”. With hardening, you remove everything that is not actually used by your application, so it cannot be abused. Sadly, there is no current option for a website to specify which Web3 actions it supports or not, in order to harden it. Therefore, with no way to harden their website and enforce this policy. As a result, PREMINT had to resort to the aforementioned informational-only route.